Home – Dark Desktop App
SOCFirst AI
Your First Line of Cyber Defense
Fully autonomous Tier 1 alert triage and investigation – no manual intervention, playbooks, code, or prompts necessary.
5x Return on Investment
Consolidate AI security tools and increase security team productivity by at least 40%
Automation Through AI
Allow for real-time detection and multi-touch takedown using AI replacing the need for a security operation team
SOC AI
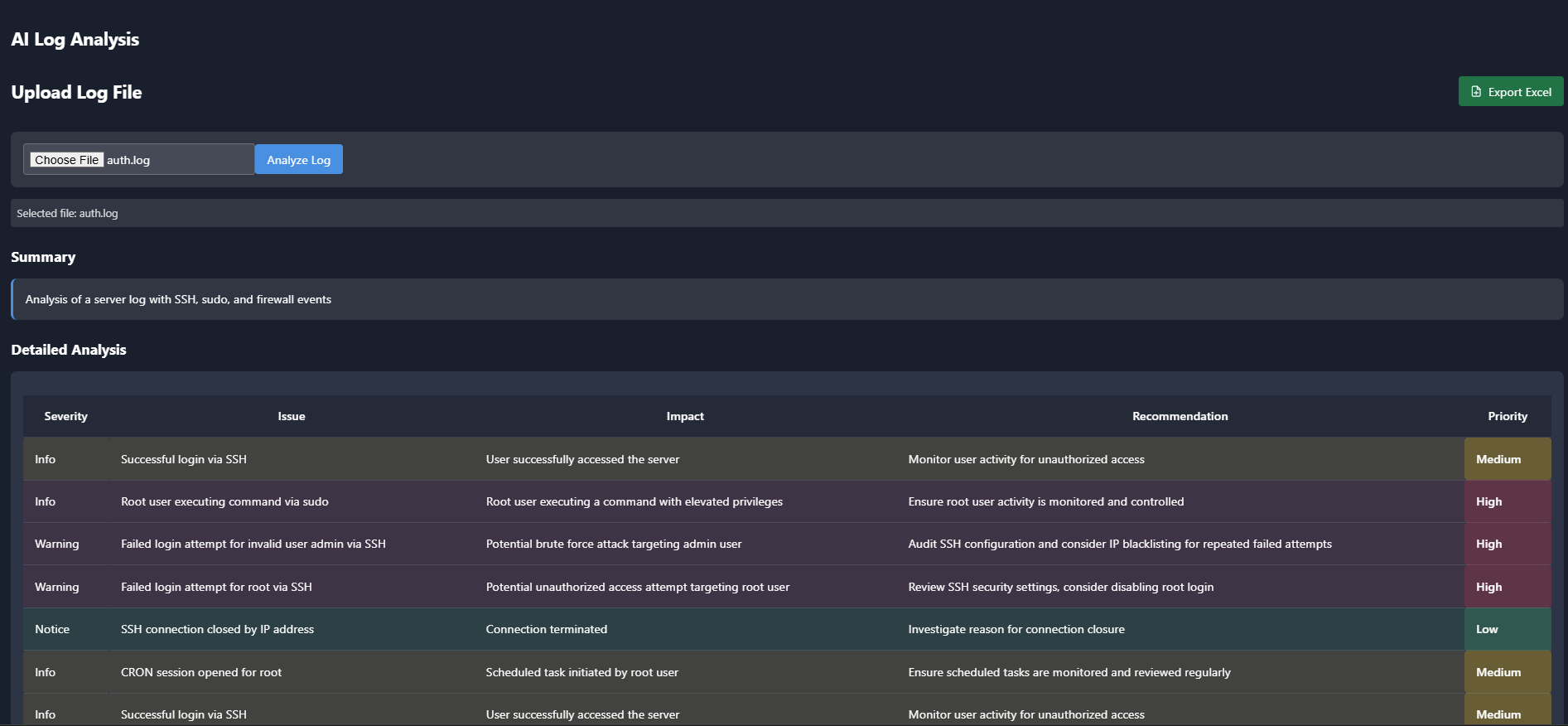
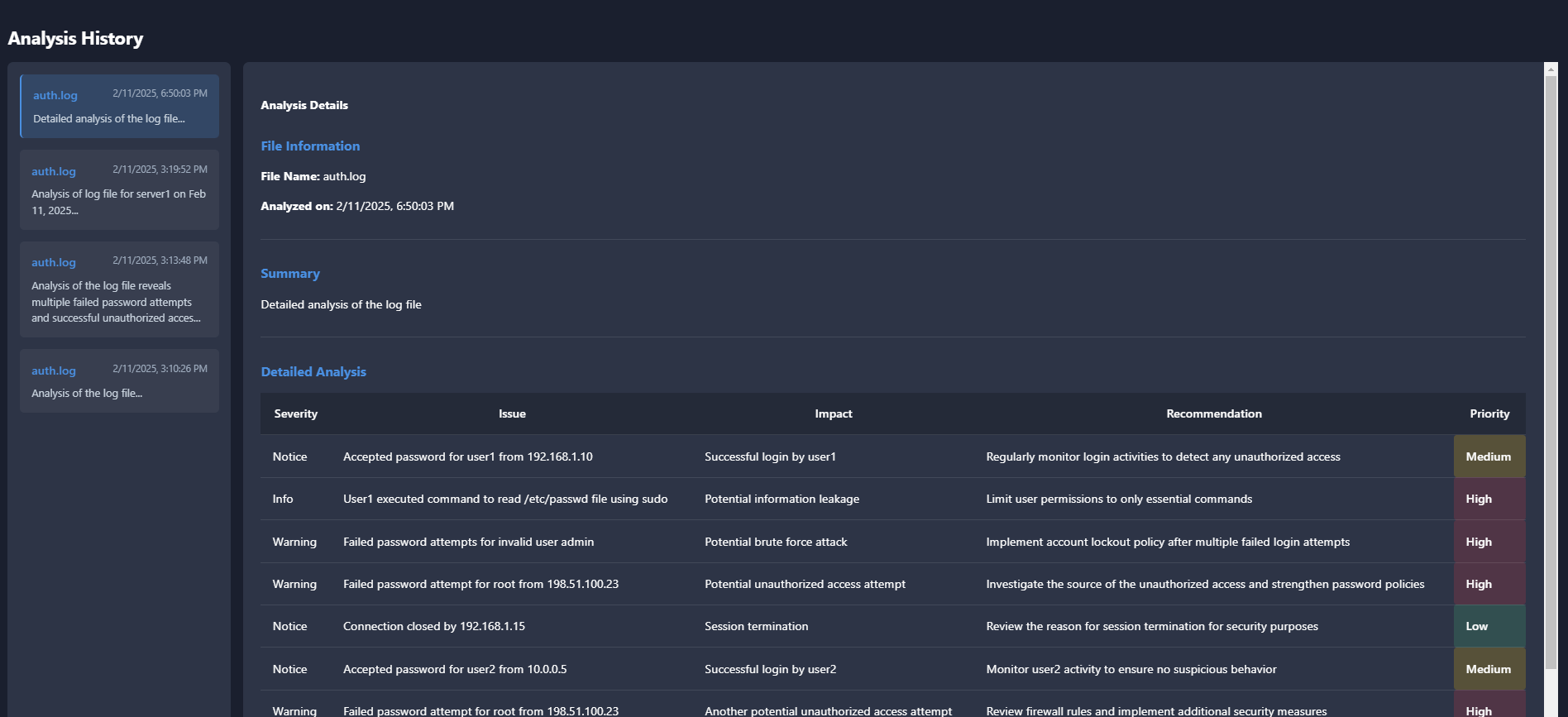
Uses artificial intelligence to detect and respond to cyber threats in real-time. Its main function is to continuously monitor and analyze security events to enhance threat detection and response capabilities.
AI-driven SOC
artificial intelligence to detect and respond to cyber threats in real-time. Its main function is to continuously monitor and analyze security events to enhance threat detection and response capabilities.
AI Analytics
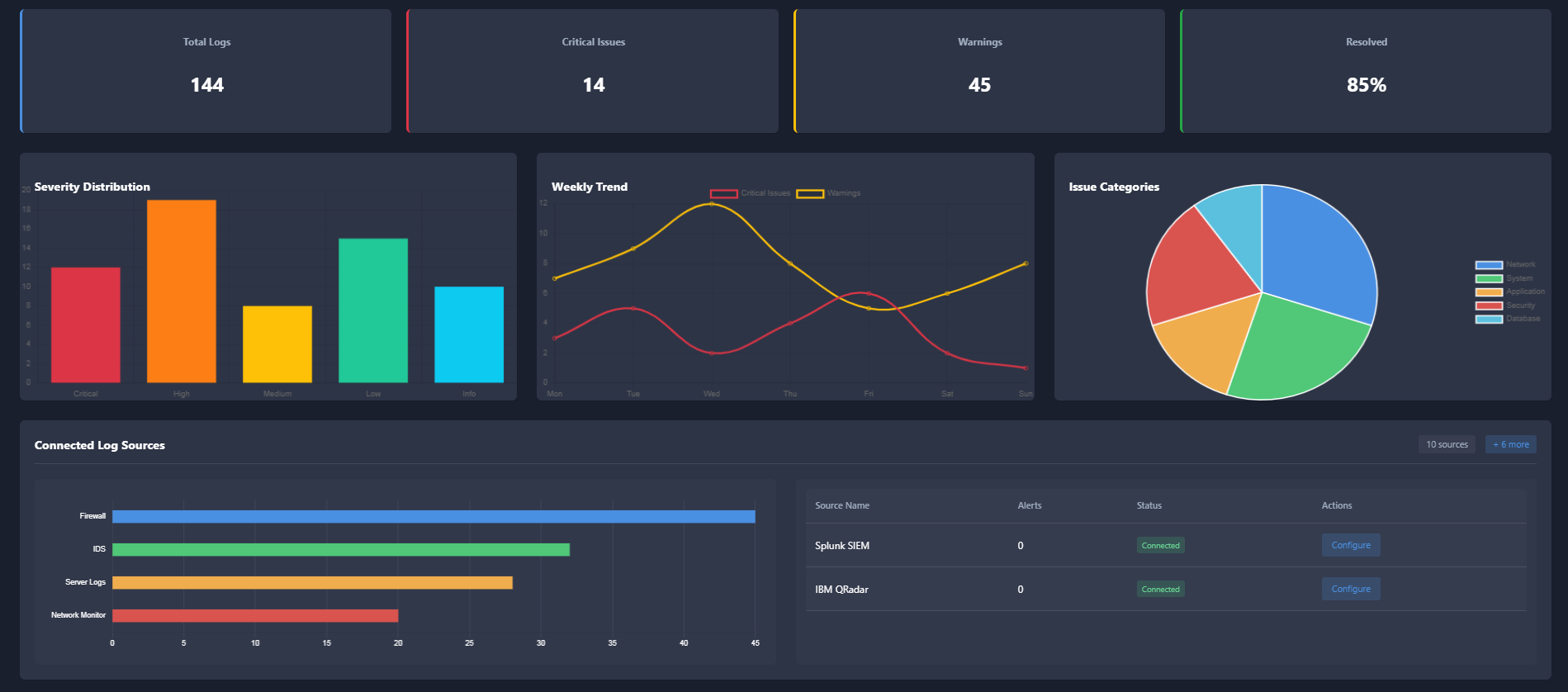
Performance
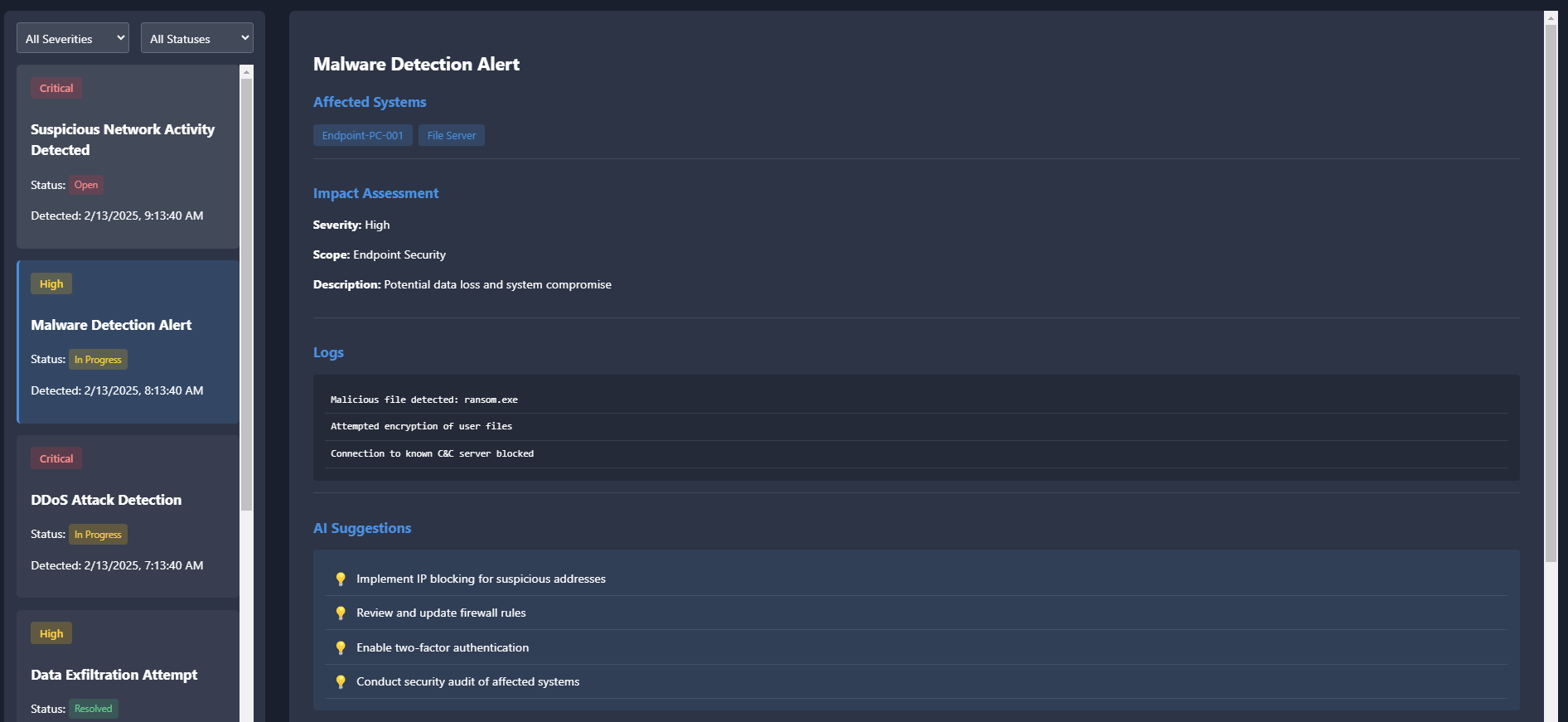
Alerts
Connect your security products
Our AI-powered SOC is designed to offer organizations a significant advantage in the fight against cybersecurity threats.
EndPoint
SOAR
SIEM
Network
CLOUD
Pricing
Starter
per month
- Basic dashboard
- Limited historial data
- 50 API connects
- 2000 request
- 5 integrations
- 8x5 Technical Support
Standard
per month
- Advanced dashboard
- Full historical data
- 150 API connects
- 5000 request
- 12 integrations
- 24/7 Support
Pro
per month
- Pro dashboard
- Full historical data
- 400 API connects
- 12000 request
- 15+ integrations
- 24/7 Priority support
AI-Driven SOC
Our AI-powered Security Operation Center is designed to offer organizations a significant advantage in the fight against cybersecurity threats.
Automatically triage and investigate every alert with the AI SOC Platform working like your Level 1 SOC to escalate only the confirmed, serious threats. Easily connect your security tools to start getting immediate value.
Automation of threat response processes to quickly neutralize potential threats.
Reduction of SOC analyst fatigue and burnout through automation of routine tasks, enabling analysts to focus on more complex threats and investigations.
Ability to identify and respond to potential threats at an unprecedented speed and accuracy.
Detection and analysis of patterns of behavior indicative of malicious activity.
Achieving a higher level of threat detection and response that traditional security methods cannot match.


