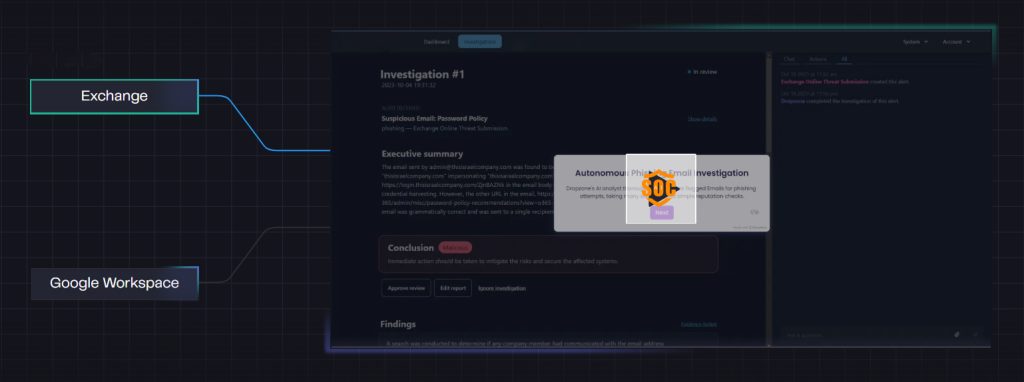
Phishing
Analyst for Phishing Alert Investigation & Email Threat Triage
Monitor
Ingests Alerts From Google WorkSpace and Office365
Extract
Identifies and Collects Evidence and Context for Every Alert
Investigate
Uncovers Hidden Threat Indicators
Triage
Prioritizes Phishing Threats Based on Risk
Remediate/Escalate
Automates Response or Escalates to Your SOC Team
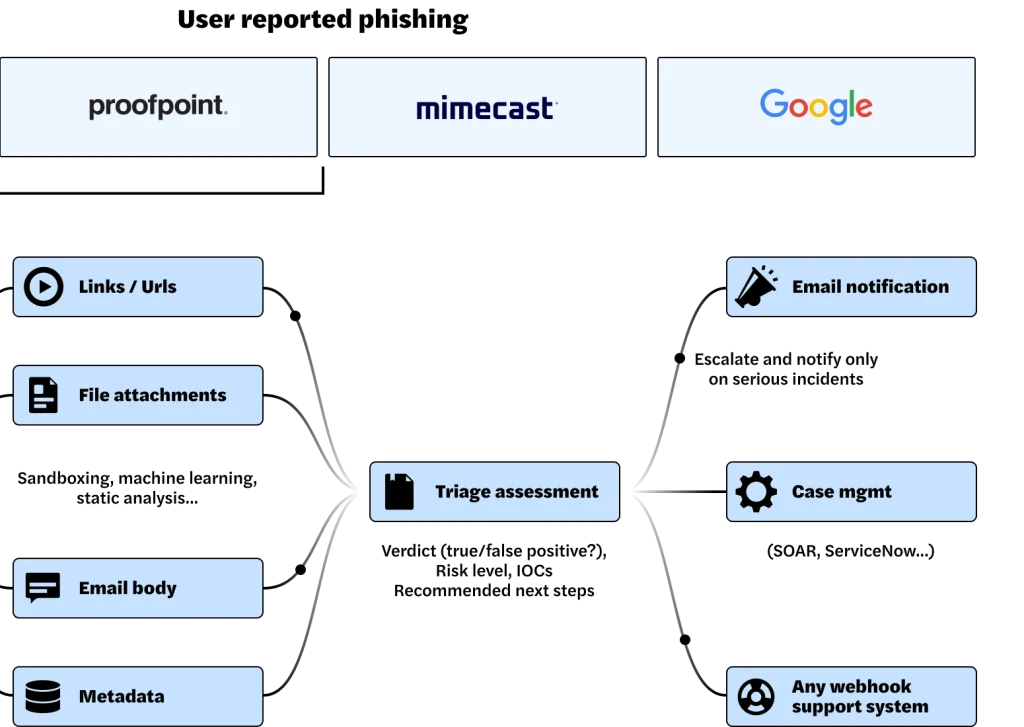
Anatomy of a Phishing Investigation
Evidence Collection
SOCFirst collects and analyzes various evidence associated with the alert to investigate it, just like a human would do, such as files and processes, command lines, related alerts about the same user or file, and information from the tool that originally fired the alert.

Threat Indicators
From the evidence, SOCFirst clearly identifies the malicious or suspicious indicators (or lack thereof) that indicate whether the email is a threat.
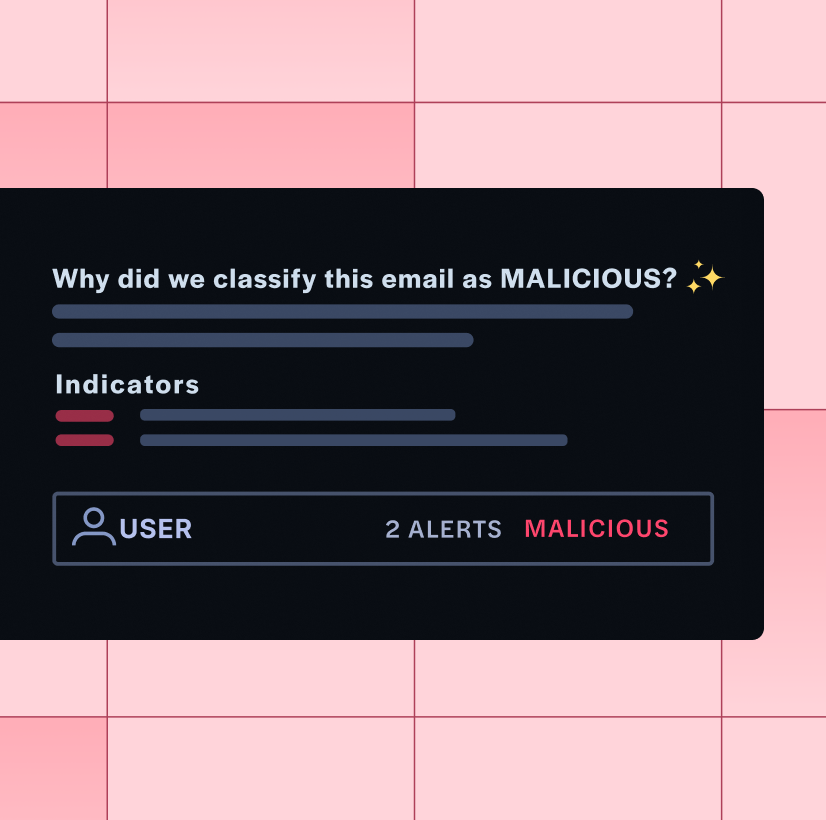
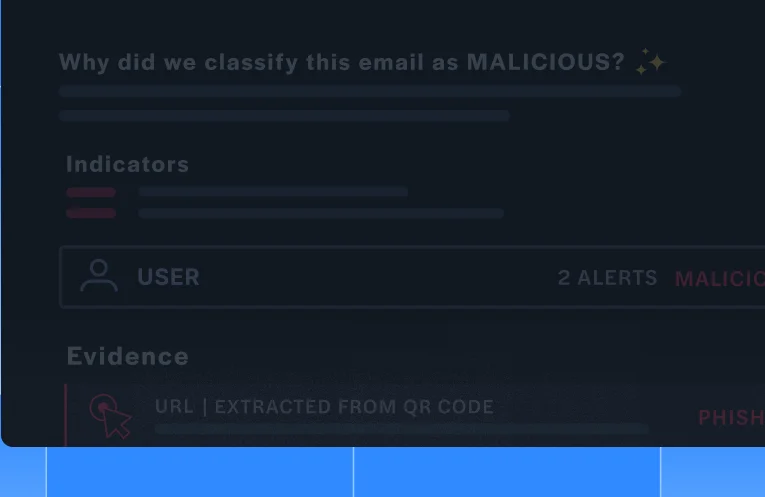
Analysis & Verdict
Taking all evidence and threat indicators into account, SOCFirst make a verdict and trigger a response (see below) if relevant. Analysts reviewing escalated (or any!) alerts have visibility into the indicators that led to the verdict, as well as a sandbox to dig in further if necessary.
Response & Recommendations
accuracy enables it to take action, dismissing and closing out cases for false positives, notifying for non-urgent issues, or escalating for critical alerts. SOCFirst can also be configured to take action itself, e.g., by blocking a user or kicking off a SOAR playbook.



